Eliminating blind spots by unifying intelligence insights across Cyber, Fraud, Physical & Compliance into a single integrated solution. Empowering organizations to prioritize, manage & respond to insider threats aligned with strategic goals & objectives.
Unified Insider Oversight
Combine insider Intel, Cyber, Fraud, Physical, and Compliance into one integrated solution.
Gain a holistic and clear view of all threats.
Break Down Silos
Connect data, controls, and detection across your ecosystem.
Enable seamless coordination between security tools and Insider Threat Management teams.
Ensure Consistency
Simplify processes, improve strategic prioritization, and standardize insider risk management.
Objectively benchmark against your peers and our comprehensive framework.
Recent statistics highlight the prevalence & impact of insider threats.
- Incidents have surged by 44% over the past 2 years.
- Average annual cost per incident has escalated to £12.14 million & rising.
- It typically takes organizations 85 days to identify & contain an insider threat.
- Over 66% of insider threat incidents result from employee negligence.
- 53% of companies consider privileged users as the top insider threat risk.
Organizations Unprepared for Insider Threats
Organizations with Technical & Strategic Investment Barriers
Challenges
Do you have fragmented systems? Disconnected processes? Delayed responses? Siloed decision-making? Confusion over where to invest for best outcomes?
What's the cost? Financial loss, regulatory breaches & damaged reputations.
Fragmented Oversight
Fragmented Oversight
Insider threats are spread across disconnected business processes, systems & tools, leading to incomplete visibility & oversight.
Silos Between Data, Controls & Detection
Silos Between Data, Controls & Detection
Teams & technologies operate in isolation, creating blind spots in threat detection & delayed responses.
Disconnected People, Processes & Technology
Disconnected People, Processes & Technology
Without a cohesive approach, misalignment between teams, manual processes & disparate tools increases operational inefficiencies.
Inconsistent Risk Management
Inconsistent Risk Management
Lack of unified intelligence hinders prioritization, making it difficult to proactively manage threats.
Strategic Investment Inefficiencies
Strategic Investment Inefficiencies
Intuition-led rather than data-driven decisions cause missed opportunities, wasted resources & competitive setbacks.
Positioning
Predict, Identify, Manage & Respond. Target Investments.
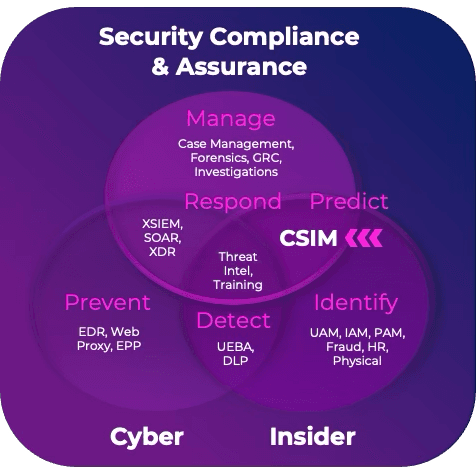
Converged Security & Insider Management (CSIM) is a new category to fill a gap within the Insider Threat product landscape.
Converging Insider Cyber, Fraud, Physical, Compliance & Assurance into one unified integrated security platform.
Illicit CSIM Platform doesn’t replace your Insider Threat controls - it integrates them to make them smarter, more connected, & more effective.
Elevates Insider Threat Management into a science by uniquely transforming the approach to insider threat security.
Insider Threat Market
Drive Smarter Strategic Investments to Target & Reduce Insider Threats.
CSIM Multi-Layer Intelligence
Insider Threat Matrix
Integrates data intelligence, threat vector analysis & operational insights to build a comprehensive view of insider risks.
Insider Threat Framework
Serves as a foundational baseline for building a holistic defense strategy, ensuring resilience against insider threats.
Transform Insider Threat Strategy with a Real-Time Dashboard
Experience a 360° view of your insider threat landscape, seamlessly integrating threat intelligence, incident data & control overlays into a single, interactive framework.
Empower Leaders, Drive Smarter Strategic Decisions
Deliver powerful, actionable insights to business leaders - providing a holistic perspective of insider risks across their areas of responsibility.
See the Unseen, Unmatched Threat Control Insights
Go beyond the limits of your current detection systems by identifying vulnerabilities flagged by external parties & overlooked by existing controls.
Prioritize What Matters, When It Matters
Respond faster & smarter. Leverage real-time threat intelligence, incident impact analysis & control data to optimize reporting, resource planning & risk mitigation.
Objective Peer Comparisons
Benchmark against peers & our comprehensive framework. Know where to invest for maximum ROI.
Introducing the power of Illicit Labs
Overview
Insider Threat Framework
Build a resilient foundation with advanced threat modeling, baseline defense strategies & comprehensive control gap analysis to eliminate vulnerabilities & strengthen your insider security posture.
Insider Threat Matrix
Turn data into actionable insights with calculated risk ratings, emerging theme analysis & correlation to uncover patterns & mitigate risks before they escalate.
Dashboard & Visualizations
Gain unparalleled visibility with real-time dashboards, dynamic heatmaps & intuitive reporting suite that empowers smarter, faster decision-making at every level.
Intelligence Driven
Stay ahead of threats with real-time intelligence, streamlined incident resolution & optimized resource allocation, ensuring a proactive & efficient approach to insider threat management.
Deployment
Full Control. Maximum Security. Tailored for Enterprise Needs.
Deployed locally for fast, responsive interfaces. Real-time dashboards for anomaly visualization.
API-first approach, docker microservices ensuring seamless integration with existing on-prem systems.
Local database with full encryption at rest & in transit. Automated backups & replication.
Deployed behind your firewall with enterprise-grade RBAC & on-premise IAM integration.
Effortless Scalability. Global Availability. SaaS Simplicity.
Collaborate globally without the hassle of managing technology.
Proactive threat monitoring, built-in access control, continuous compliance with enterprise-grade security standards.
All functionality is available to you via our secure APIs - no vendor lock-in.
Securing your data with keys for your company only.
Holistic Threat Intelligence
Access real-time dashboards with global heatmaps, emerging themes & comprehensive reports to visualize insider risks & take immediate action.
Prioritize What Matters Most
Focus on high-impact threats with advanced analytics that assess financial, operational & reputational risks. Surface strategic priority investments.
Benchmark Against Peers
See how you compare to peers without revealing any sensitive data that could compromise your security or sensitive data processing needs. Compare against performance metrics, control coverage & more.
Insider Threat Lifecycle Coverage
Proactively track & mitigate threats at every stage. From motive & planning to execution & beyond with dynamic kill chain analysis & control gap detection.
Proven Control Effectiveness
Strengthen your defenses with policy & control management tools that pinpoint vulnerabilities & boost compliance.
Smart Resource Allocation
Optimize workload management with active & backlog tracking for your team. Ensuring the right resources are in place to handle threats efficiently.
Get in Touch
We would love to hear from you! Reach out with any queries or if you require any further information.